New Variant of Conficker/Downadup Worm Circulating
added February 23, 2009 at 05:02 pm
*For Immediate remote support in removing Conficker B++, call (509) 438-0990. For more info, please visit LIVE SUPPORT.
US-CERT is aware of public reports concerning a new variant of the Conficker/Downadup worm, named Conficker B++. This variant propagates itself via multiple methods, including exploitation of the previously patched vulnerability, password guessing, and the infection of removable media. Most significantly, Conficker B++ implements a new backdoor with “auto-update” functionality, allowing machines compromised by the new variant to have additional malicious code installed on them. According to Microsoft, there is no indication that systems infected with previous variants of Conficker can automatically be re-infected with the B++ variant.
US-CERT strongly encourages users to update unpatched systems as soon as possible.
Additionally, US-CERT recommends that users take the following preventative measures to help mitigate the security risks:
Install antivirus software, and keep the virus signatures up to date.
- Review the Microsoft Malware Protection Center blog entry for details regarding the worm.
- Review the Using Caution with USB Drives Cyber Security Tip for more information on protecting removable media.
Conficker A/B Top-Level Control Flow
Figure 1 illustrates a flow diagram of the main thread for both variants of the Conficker agent, A and B. In both cases, the Conficker agent is distributed and run as a dynamically linked library. Its base code has been compiled as a DLL and its DLLMain function initiates the main thread represented by the diagram. The agent code proceeds by first checking the Windows version, and based on this result creates a remote thread in processes such as svchost.exe. This is done by invoking LoadLibrary, where the copy of the DLL is passed as an argument. The malicious library then copies itself in the system root directory under a random file name. After initiating the use of Winsock DLL, the bulk of the malicious code logic is executed.
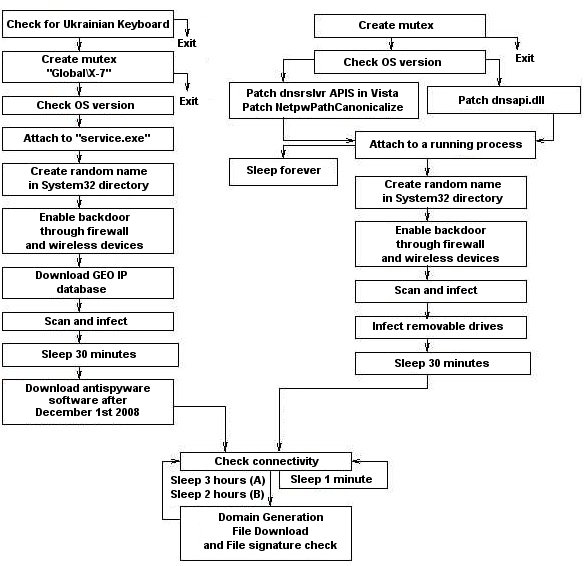
Figure 1: Conficker A (left) /B (right): Top-level control flow
Conficker A’s agent proceeds as follows. First, it checks for the presence of a firewall. If a firewall exists, the agent sends a UPNP message to open a local random high-order port (i.e., it asks the firewall to open its backdoor port to the Internet). Next, it opens the same high-order port on its local host: its binary upload backdoor. This backdoor is used during propagation, to allow newly infected victims to retrieve the Conficker binary. It proceeds to one of the following sites to obtain its external-facing IP address http://www.getmyip.org, getmyip.co.uk, and checkip.dyndns.org, and attempts to download the GeoIP database from maxmind.com. It randomly generates IP addresses to search for additional victims, filtering Ukraine IPs based on the GeoIP database. The GeoIP information is also used as part of MS08-67 exploit process [10]. Conficker A then sleeps for 30 minutes before starting a thread that attempts to contact http://trafficconverter.biz/4vir/antispyware/ to download a file called loadadv.exe. This thread cycles every 5 minutes.
Next, Conficker A enters an infinite loop, within which it generates a list of 250 domain names (rendezvous points). The name-generation function is based on a randomizing function that it seeds with the current UTC system date. The same list of 250 names is generated every 3 hours, i.e., 8 times per day. All Conficker clients, with system clocks that are at minimum synchronized to the current UTC date, will compute and attempt to contact the same set of domains. When contacting a domain for which a valid IP address has been registered, Conficker clients send a URL request to TCP port 80 of the target IP, and if a Windows binary is returned, it will be validated via a locally stored public key, stored on the victim host, and executed. If the computer is not connected to the Internet, then the malicious code will check for connectivity every 60 seconds. When the computer is connected, Conficker A will execute the domain name generation subroutine, contacting every registered domain in the current 250-name set to inquire if an executable is available for download.
Conficker B is a rewrite of Conficker A with the following noticeable differences. First, Conficker A incorporates a Ukraine-avoidance routine that causes the process to suicide if the keyboard language layout has been set to Ukrainian. Conficker B does not include this keyboard check. B also uses different mutex strings and patches a number of Windows APIs, and attempts to disable its victim’s local security defenses by terminating the execution of a predefined set of antivirus products it finds on the machine. It has significantly more suicide logic embedded in its code, and employs anti-debugging features to avoid reverse engineering attempts.
Conficker B uses a different set of sites to query its external-facing IP address http://www.getmyip.org, http://www.whatsmyipaddress.com, http://www.whatismyip.org, checkip.dyndns.org. It does not download the fraudware Antivirus XP software that version A attempts to download. Conficker’s propagation methods vary among A and B and are described in Section Conficker Propagation. Furthermore, a recent analysis by Symantec has uncovered that the GeoIP file is directly embedded in the Conficker B binary as a compressed RAR (Roshal archive) file encrypted using RC4 [11].
Like Conficker A, after a relatively short initialization phase followed by a scan and infect stage, Conficker B proceeds to generate a daily list of domains to probe for the download of an additional payload. Conficker B builds its candidate set of rendezvous points every 2 hours, using a similar algorithm. But it uses different seeds and also appends three additional top-level domains. The result is that the daily domain lists generated by A and B do not overlap.
Binary Download and Validation
Among the key functions of Conficker is that of probing the daily set of Internet rendezvous points for a new Windows executable file to download and execute. This mechanism provides an effective binary updating service similar to that of other traditional botnets, with the exception that the Conficker update service is highly mobile and its location (i.e., to date we have not confirmed this feature in use by the malware authors) is recomputed each day by all infected clients. Although many groups have been able to break the domain generation algorithm and registered rendezvous points, Conficker’s authors have taken care to ensure that other groups cannot upload arbitrary binaries to its infected drones.
Both Conficker A and B clients incorporate a binary validation mechanism to ensure that a downloaded binary has been signed by the Conficker authors. Figure 2 illustrates the download validation procedure used to verify the authenticity of binaries pulled from Internet rendezvous points. The procedure begins with Conficker’s authors computing a 512-bit hash M of the Windows binary that will be downloaded to the client. The binary is then encrypted using the symmetric stream cipher RC4 algorithm with password M. Next, the authors compute a digital signature using an RSA encryption scheme, as follows: M^epriv mod N = Sig, where N is a public modulus that is embedded in all Conficker client binaries. Sig is then appended to the encrypted binary, and together they can be pushed to all infected Conficker clients that connect to the appropriate rendezvous point.